What Marketo users need to know about Gmail and Yahoo’s new email authentication requirements

No doubt you’re already busy with the new sender requirements that are coming into force at Gmail and Yahoo starting in February 2024. If you haven’t already, be sure to review all the official guidance from both Gmail and Yahoo to ensure you’ll be ready.
The requirements fall roughly into two categories: sender best practices to keep spam rates low, and technical authentication requirements.
The main technical requirements will be our focus in this article.
If you’ve read through them, you will have noticed that some of the requirements seem to be aimed at the organizations like Adobe who actually run email sending platforms like Adobe Marketo Engage, while some are aimed at the people who use those platforms — and they’re all jumbled up together.
If you’re a Marketo user, how do you know which changes actually apply to you, and which changes are Marketo’s responsibility?
In this article we’ll go over the major authentication and technical requirements, what they mean, and most importantly, who is responsible.
But first up, there are a few key concepts that are important to know about. Before we dive in, we’ll go over them.
Please note: This guide is not exhaustive but is designed to complement the official guidance, so be sure to use the requirements from both Gmail and Yahoo as your official checklists for the change.
Before we begin: key concepts to know
Bulk senders according to Gmail and Yahoo
Gmail says a “bulk sender” is any domain in the “From:” address that sends 5,000 messages a day to recipients at gmail.com and googlemail.com addresses.
Yahoo defines it as “an email sender sending a significant volume of mail”. They specifically state, “we will not specify a volume threshold.”
Message header
When reading the requirements there are a lot of mentions of the ‘message header’.
This is not the top banner in your email’s design, nor is it even the <head> element in the HTML document. The message header is at the top of the outer wrapper of the entire email. It contains all the sender and receiver information, the plain text version, and the HTML version of your email.
You don’t see the message header unless you go looking for it, which you can do in Gmail by going to the three-dot menu on the top right of a message and clicking ‘Show Original’.
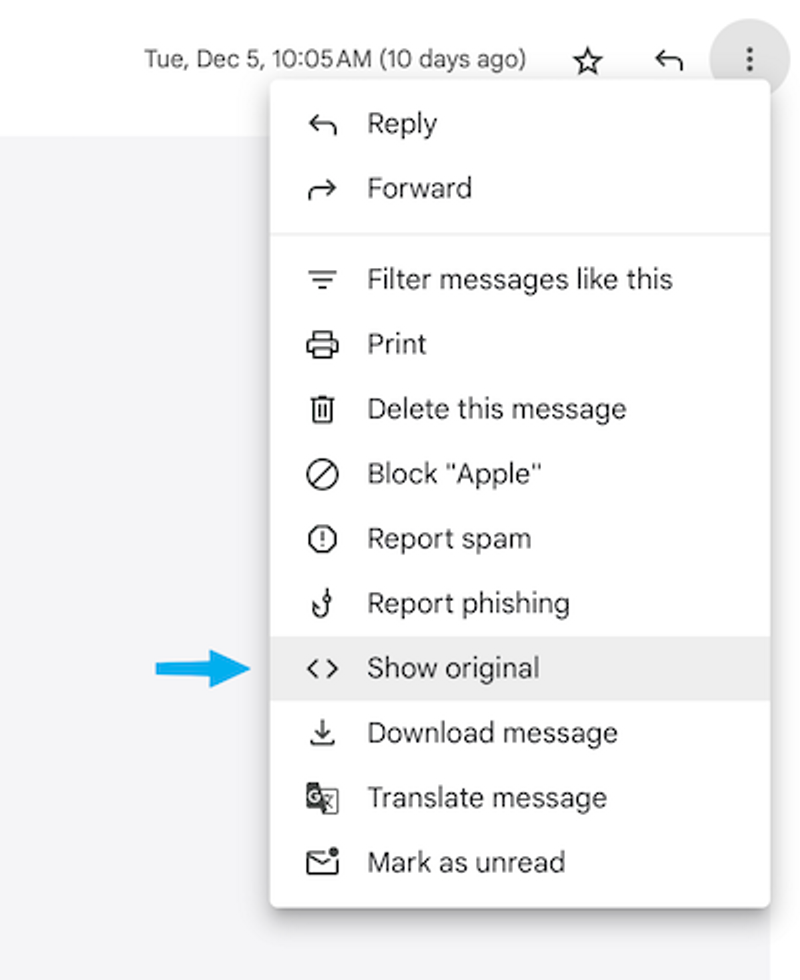
You will see the ‘raw’ message, and the code at the top is all of the message header. Further down below this there will be a ‘part’ with your plain text email, and then a part with your email’s HTML.
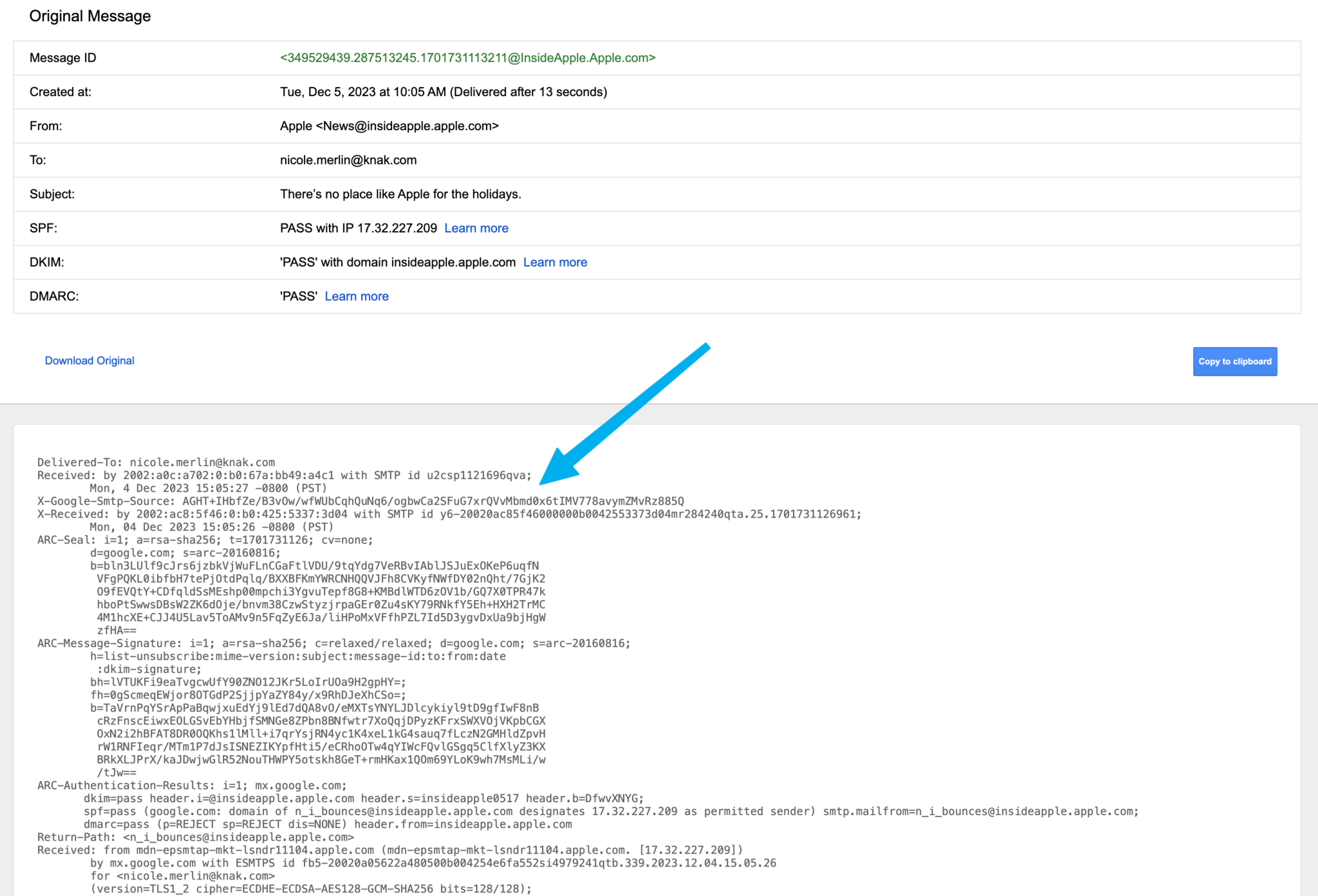
The message header is indicated at the top of this code.
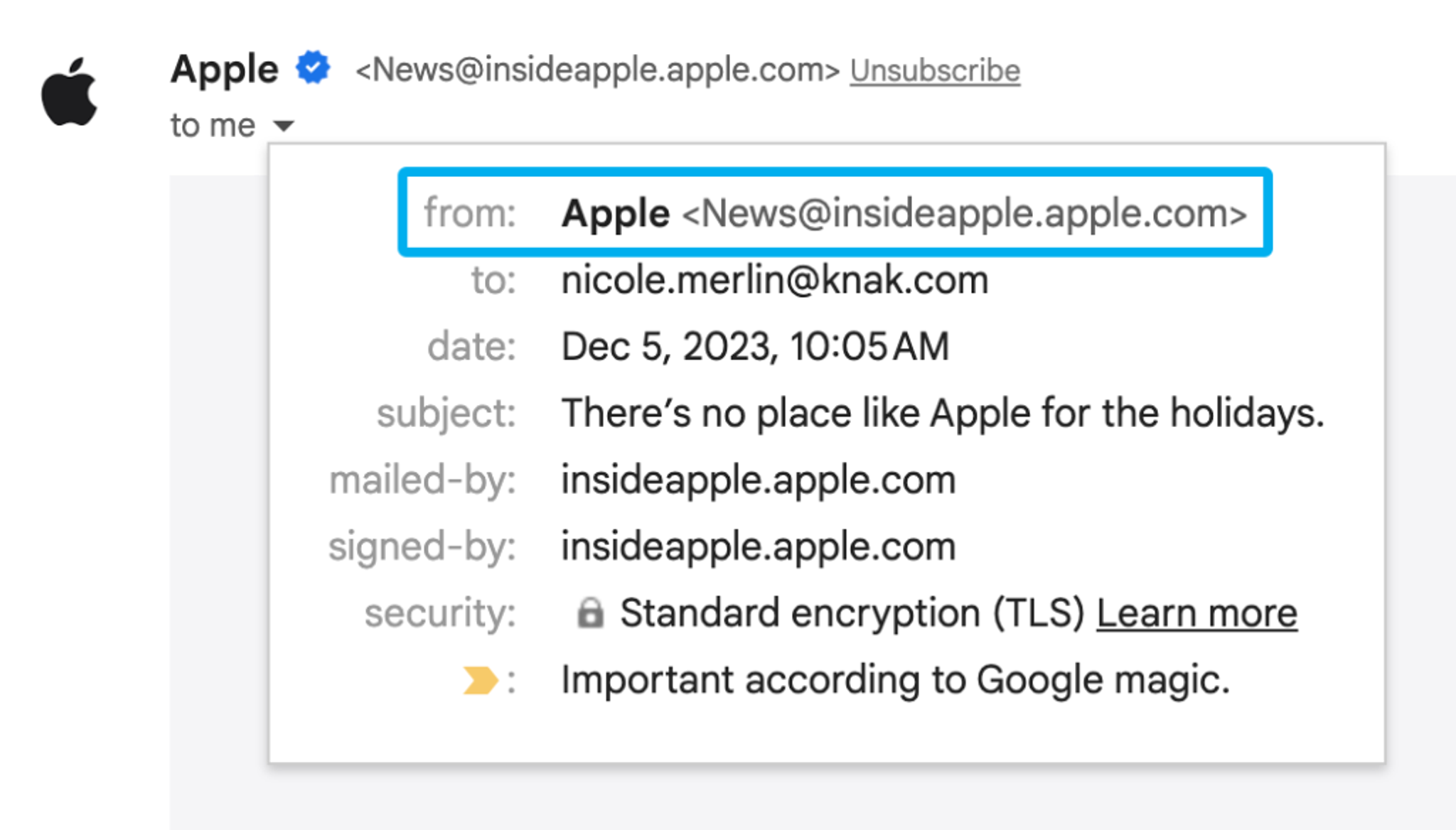
‘From:’ address
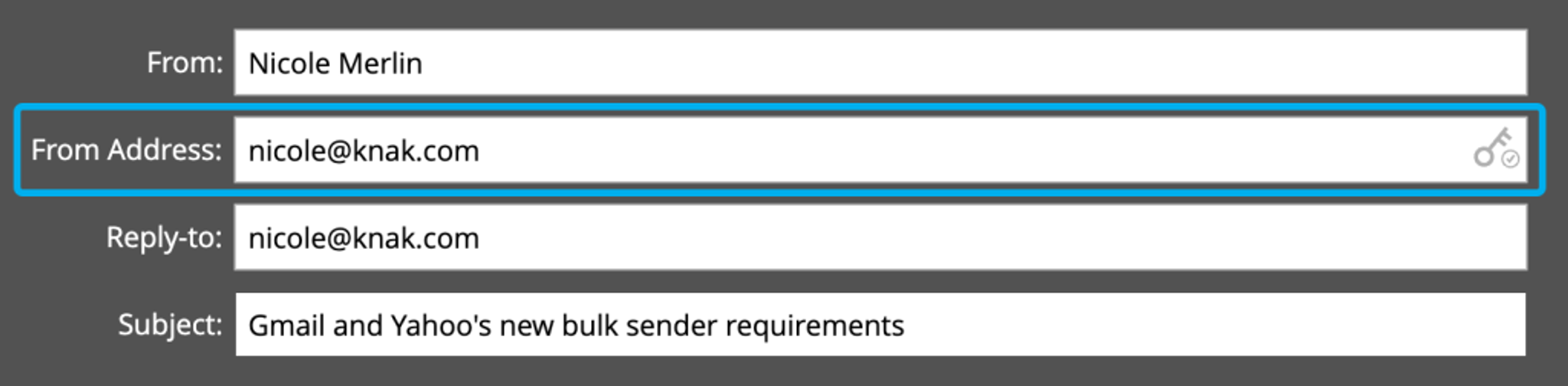
When Gmail and Yahoo are talking about the ‘From:’ address, they mean this one which can be seen marked as such in the inbox:
It’s the “From Address” field when creating an email in Marketo:
‘Return-Path’ address
This is not the same as the ‘From:’ address above. This is the email address that actually sends your message, and the address that would receive any bouncebacks. Gmail sometimes calls this the ‘Envelope sender address’.
A recipient does not usually see the Return-Path address, unless they inspect the sender details more closely.
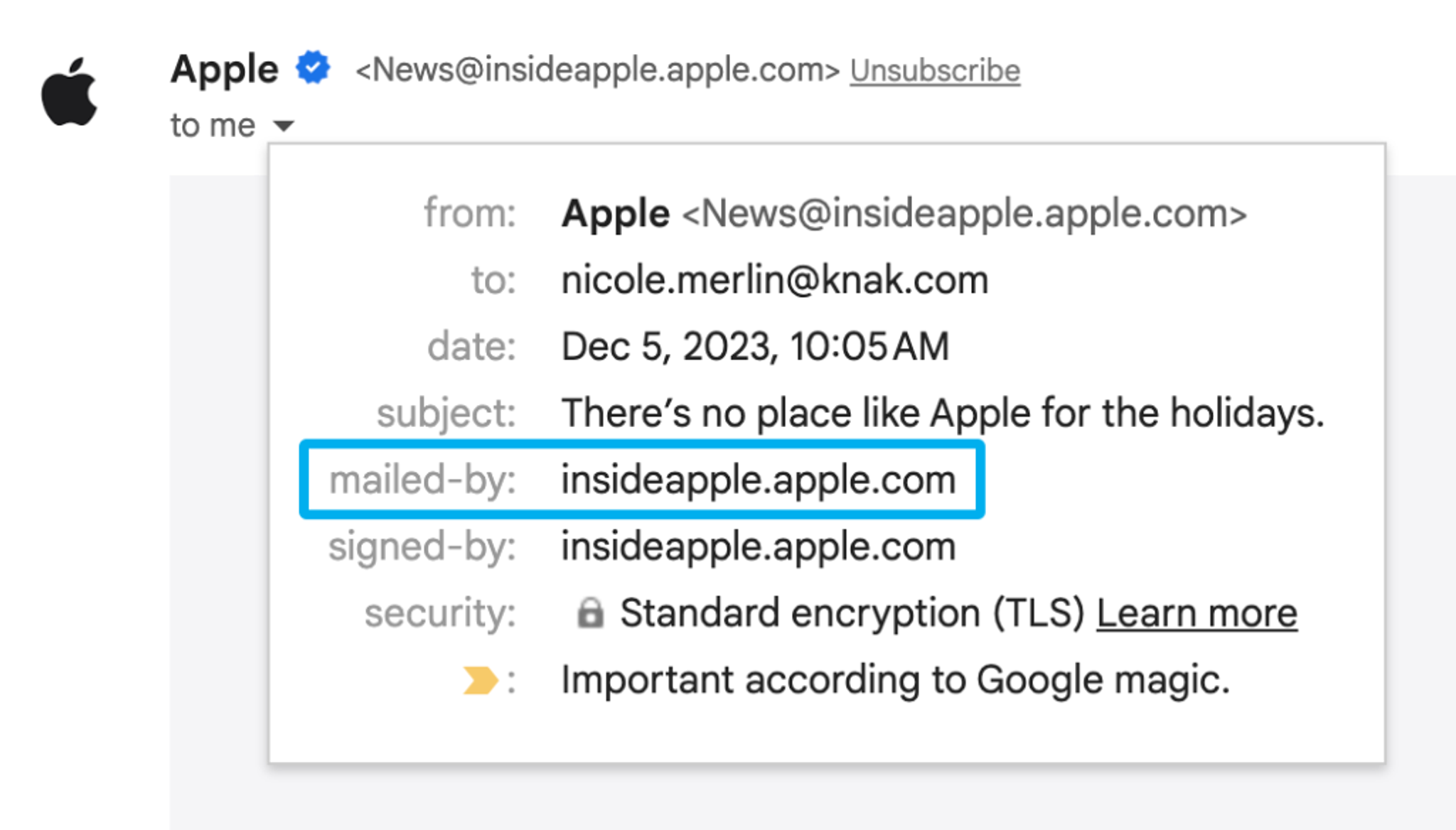
It is the mailed-by heading shown here in Gmail on our example from Apple:
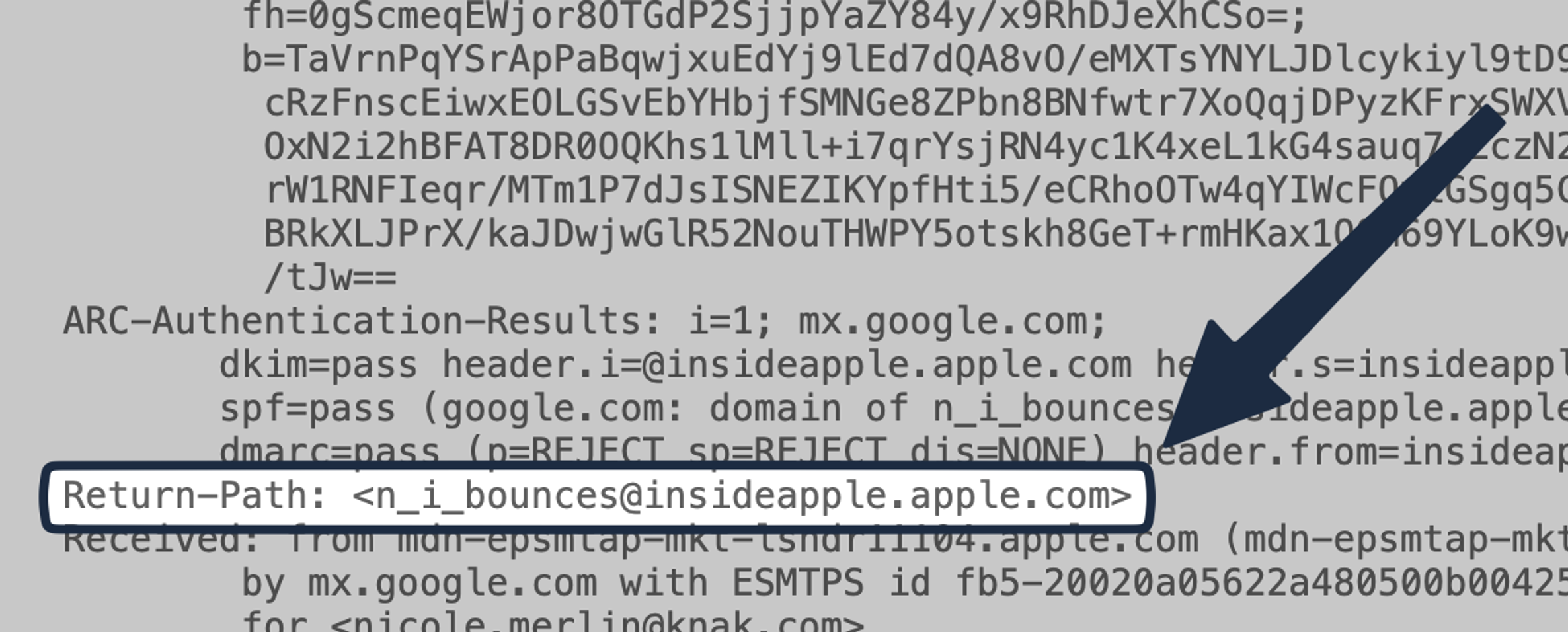
And if we open the Message Header again, you can find it in the message code:
Branded and non-Branded Return Paths at Marketo
We’ll cover this in more detail below, but Marketo offers both Branded and non-Branded Return Paths, and you will be using one or the other.
If you have a non-Branded Return Path setup on Marketo, your Return-Path address is an address that ends in mktomail.com.
If you use a ‘Branded Return Path’ with Marketo, your Return-Path address will be a subdomain on your organization’s domain which was configured by Marketo and your Marketo instance administrator.
Read more at Marketo about Branded Return Path (envelope_from) on Shared or Trusted IPs and Branded Return Path (envelope_from) on Dedicated IPs.
The Gmail and Yahoo bulk sender requirements for Marketo users
SPF (Sender Policy Framework) authentication requirements
| For all senders | For bulk senders |
|---|---|---|
Gmail’s requirement | You must have either an SPF record or a DKIM record published on your domain | |
Yahoo’s requirement | You must have either an SPF record or a DKIM record published on your domain |
| Gmail’s requirement |
|---|---|
For all senders | You must have either an SPF record or a DKIM record published on your domain |
For bulk senders |
| Yahoo’s requirement |
|---|---|
For all senders | You must have either an SPF record or a DKIM record published on your domain |
For bulk senders |
SPF authentication is all about verifying that the IP address where a message originated is actually authorized to send mail from the sender’s address. For SPF, the ‘sender’s address’ is the Return-Path address. To verify SPF authentication, mail receivers like Gmail and Yahoo look up the domain in the Return-Path address and seek out an SPF record (a type of DNS record) on that domain which authorizes the IP address which actually sent the email.
The SPF requirement may be Marketo’s responsibility, or it may be your organization’s, depending on whether you use a standard or a Branded Return Path with Marketo.
You can quickly check to see the Return-Path domain of your emails in Gmail by clicking the small arrow next to the sender name. It’s labeled ‘mailed-by’:
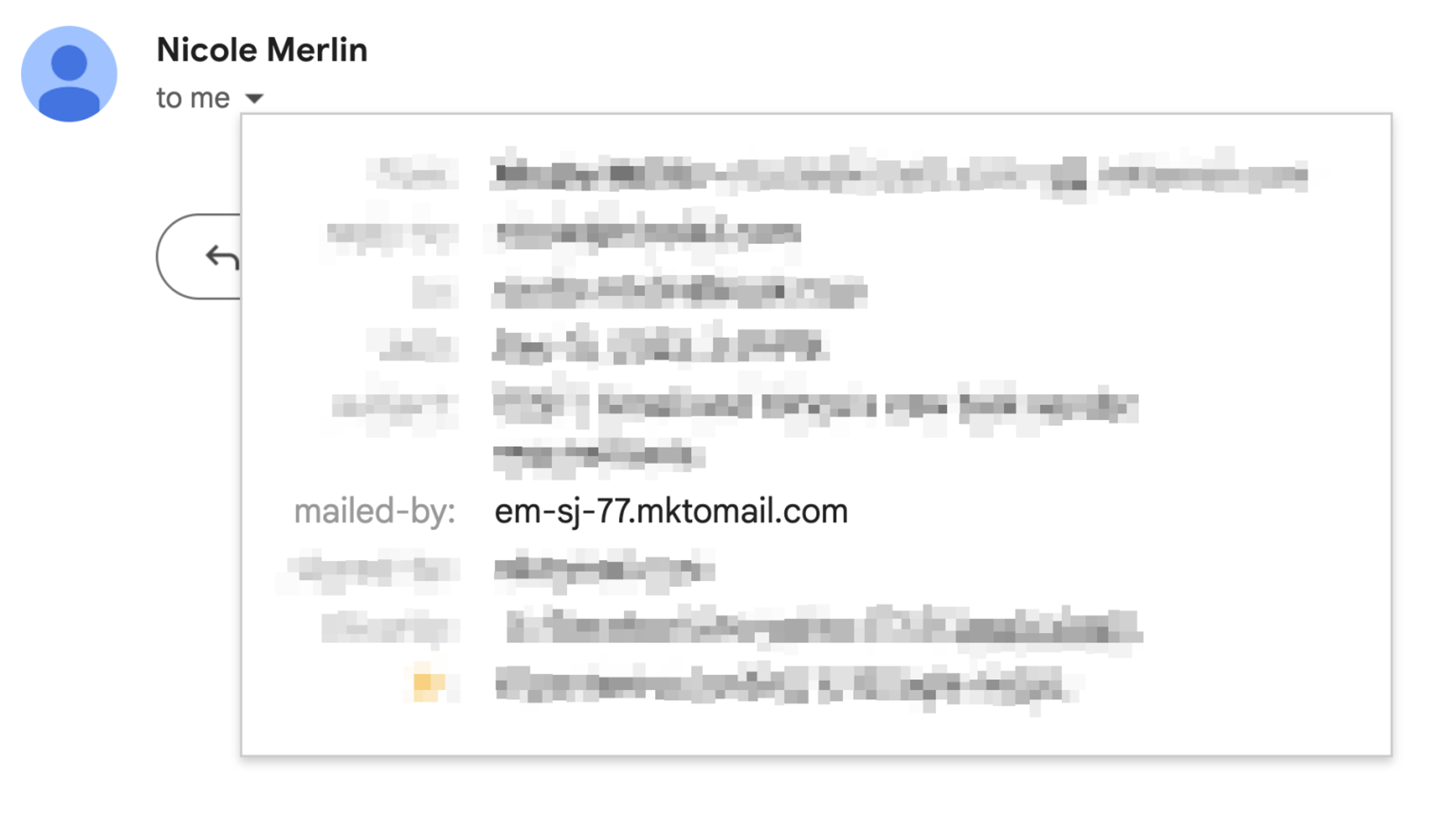
If this ends in mktomail.com then you are on a standard Return Path. If it contains a custom domain related to your organization, you are on a Branded Return Path.
SPF on a Marketo standard Return Path
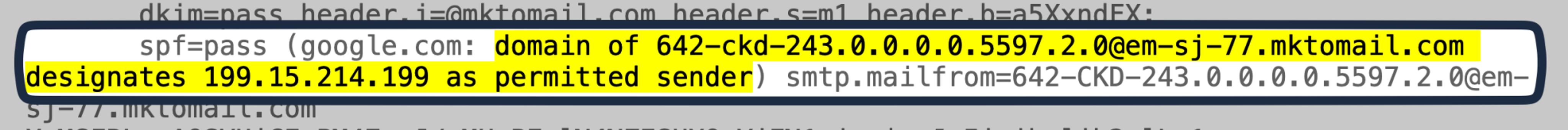
Marketo’s standard Return-Path addresses are subdomains ending mktomail.com, for example em-sj-77.mktomail.com. For this example, SPF authentication would look up em-sj-77.mktomail.com and seek out an SPF record approving the sender IP address.
Marketo publishes SPF records on its domains authorizing all of its own IP addresses, so this will exist, and SPF will pass authentication.
You can see this result in the message header:

You can see further detail if you dig into the message header and search for spf=pass:
SPF on a Branded Return Path
If you are on a Branded Return Path, then the mail receiver will seek out the Return-Path domain, like news.yourdomain.com, and look for an SPF record there which authorizes Marketo’s sending IP addresses. As above, you can see this result by viewing any email’s Message Header in Gmail.
This is likely managed by your network administrator in conjunction with your Marketo instance administrator and Marketo.
Marketo’s instructions for setting up a Branded Return Path on either shared or trusted IPs or dedicated IPs also include the instructions for configuring SPF at the same time.
Marketo also provides general instructions for configuring SPF here.
SPF Alignment and DMARC
The above relates to the requirement for SPF authentication. There is an additional requirement that may apply to you for SPF alignment. See the table below for an explanation of the difference and our section on DMARC for more information.
DKIM (DomainKeys Identified Mail) authentication requirements
| For all senders | For bulk senders |
|---|---|---|
Gmail’s requirement | You must have either an SPF record or a DKIM record published on your domain | |
Yahoo’s requirement | You must have either an SPF record or a DKIM record published on your domain |
| Gmail’s requirement |
|---|---|
For all senders | You must have either an SPF record or a DKIM record published on your domain |
For bulk senders |
| Yahoo’s requirement |
|---|---|
For all senders | You must have either an SPF record or a DKIM record published on your domain |
For bulk senders |
DKIM is a system for proving that emails belong to the organization that they claim to belong to. It has two parts: a digital signature that goes out on every email which declares a ‘parent’ web domain, and a DNS record on that domain with a matching signature that confirms the two are an authentication pair.
This means there are two parts to setting up DKIM: configuring Marketo to include the correct digital signature on every sent email, and ensuring the correct DNS record is configured on the web domain.
You may be using a shared DKIM signature or a custom DKIM signature.
When editing an email, Marketo displays a small key icon in the ‘From:’ address field which reflects whether the domain you have entered in the email address is set up with a custom DKIM signature in Marketo or not:
If you are using a custom DKIM signature, the key icon will be green:

If you have not configured a custom DKIM signature
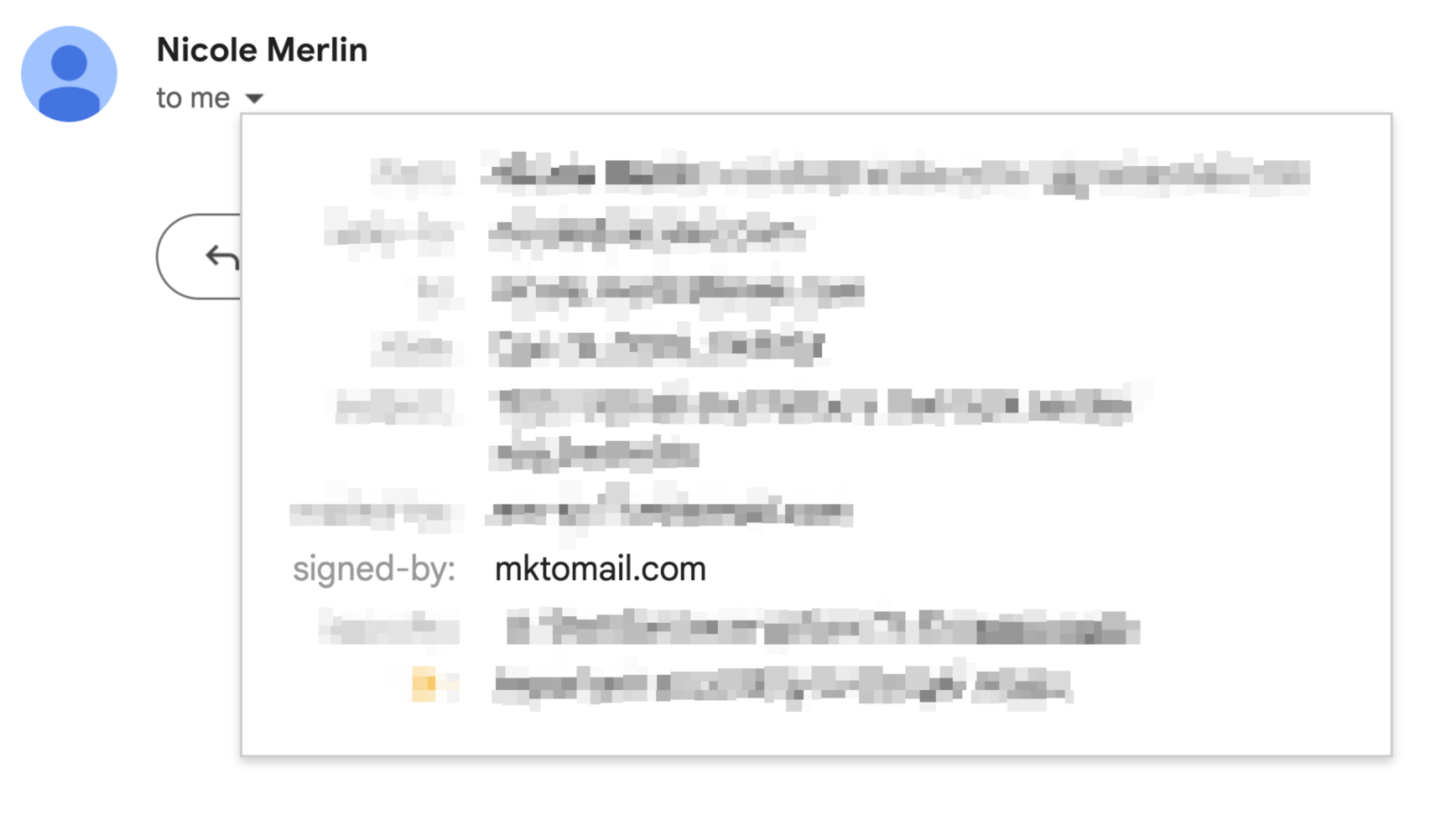
Marketo does automatically sign all outbound mail with a ‘shared Marketo DKIM signature’ which references their sender domain, e.g. mktomail.com, which is also the domain where their corresponding DKIM record is stored. This enables a DKIM authentication pass for mktomail.com.
You can see the DKIM domain in the sender dropdown in Gmail, where it’s marked as ‘signed-by’:
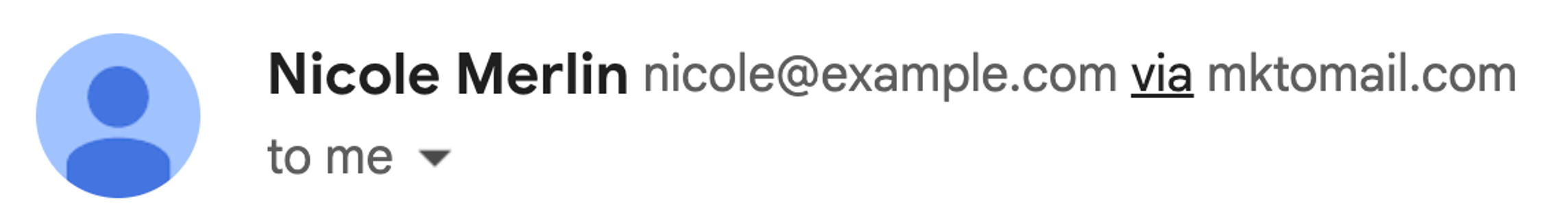
However relying on Marketo’s DKIM is not ideal, because when you write an email address at your organization’s domain into the ‘From:’ field in Marketo, the received message in Gmail will say that it is from “you@yourcompany.com via mktomail.com” because yourcompany.com and mktomail.com are different:
Additionally, this setup will be problematic when it comes to the DKIM alignment requirement (which we discuss in the DMARC section below) because of the fact that mktomail.com is not related to the domain in your ‘From:’ address, meaning they do not ‘align’.
It is best to ensure DKIM alignment, not just so it looks a little better in the inbox, but also as it’s one of the simpler ways to meet the new requirements, even for bulk senders.
Using a custom DKIM signature
To set up a DKIM signature that references your domain, you need to set the DKIM record up on the domain you want to use in your ‘From:’ address, and then configure Marketo to send out a copy of the matching digital signature on every email that they send for you.
As the DKIM record lives on your domain, it would typically be managed by your network administrator. To configure the DKIM key in Marketo, check out their guide to setting up a custom DKIM signature in Marketo.
DKIM Alignment and DMARC
The above relates to the requirement for DKIM authentication. There is an additional requirement that may apply to you for DKIM alignment. See the table below for an explanation of the difference and our section on DMARC for more information.
DMARC: Domain-based Message Authentication, Reporting & Conformance requirements
| For all senders | For bulk senders |
|---|---|---|
Gmail’s requirement | You must set up a DMARC policy, no enforcement is fine. Also see additional DMARC alignment requirements below. | |
Yahoo’s requirement | Publish a valid DMARC policy, no enforcement is fine. Also see additional DMARC alignment requirements below. |
| Gmail’s requirement |
|---|---|
For all senders | |
For bulk senders | You must set up a DMARC policy, no enforcement is fine. Also see additional DMARC alignment requirements below. |
| Yahoo’s requirement |
|---|---|
For all senders | |
For bulk senders | Publish a valid DMARC policy, no enforcement is fine. Also see additional DMARC alignment requirements below. |
DMARC allows you to declare the levels of SPF and DKIM authentication that you are committed to, as well as what email receivers should do with messages that don’t meet those levels.
Marketo has published guidelines for complying with DMARC here. Gmail also links to some helpful generic information on DMARC which helps explain some of the core concepts, like the different enforcement policy levels.
In terms of actually adding the DMARC record, this step is fairly simple, as both Gmail and Yahoo are happy for you to set an enforcement policy of “none”, which has no real effect on anything. The DMARC record itself is another DNS record, and as such it would typically be set up by your network administrator on your organization’s web domain.
You can see if a message is passing DMARC in Gmail by viewing the Message Header. Here is where you will see a report of all the authentication. In this example we can see a pass with flying colors from Apple:
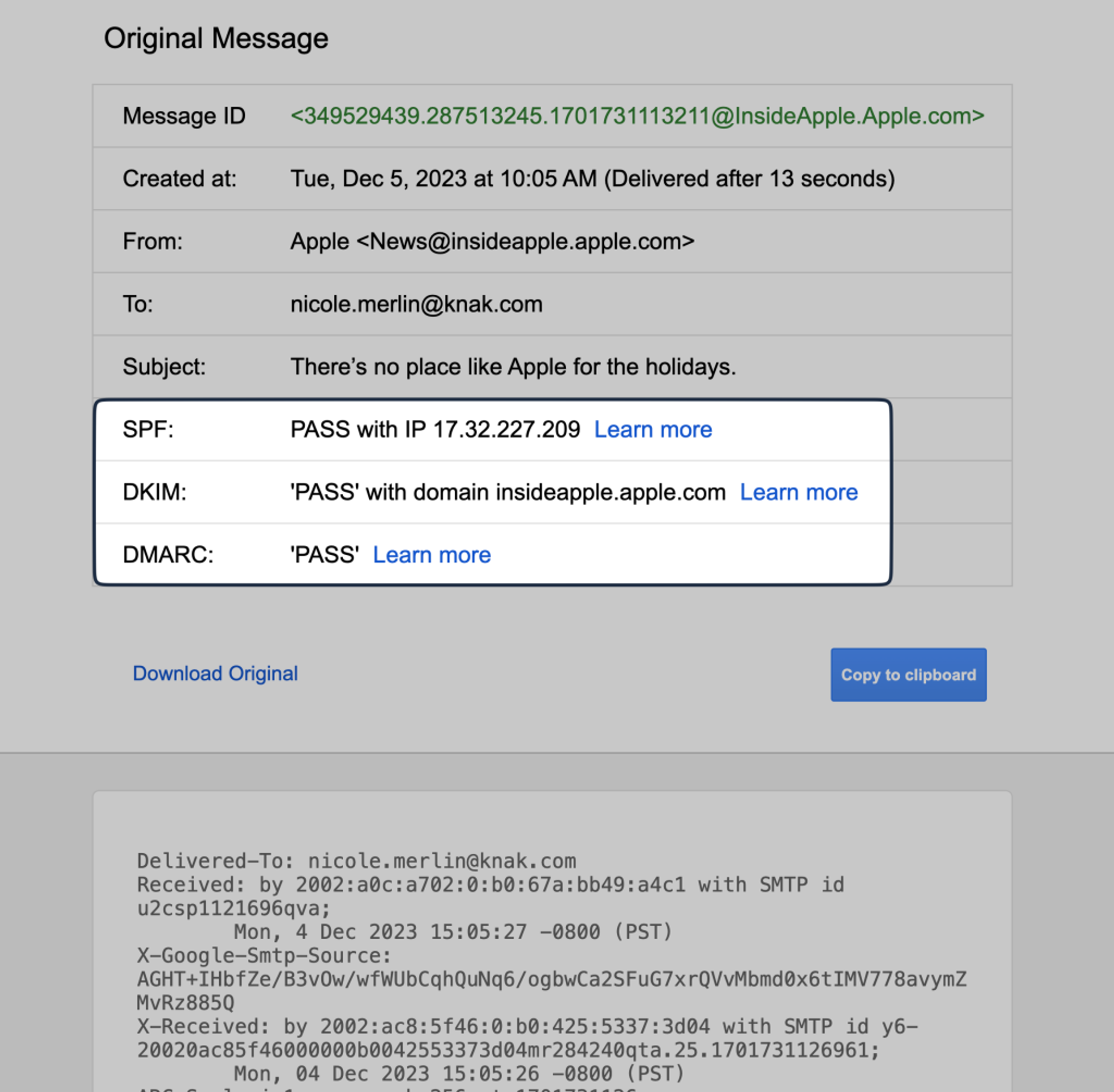
Arguably the tricker part is DMARC alignment, which we’ll go over below.
Passing DMARC with Alignment
| For all senders | For bulk senders |
|---|---|---|
Gmail’s requirement | ||
Yahoo’s requirement |
| Gmail’s requirement |
|---|---|
For all senders | |
For bulk senders |
| Yahoo’s requirement |
|---|---|
For all senders | |
For bulk senders |
To be compliant as a bulk sender, you also need to ‘pass’ DMARC on the basis of either DKIM or SPF alignment.
For the purposes of alignment, DMARC will check the ‘From:’ address and how closely it matches the domain used for SPF or DKIM.
Gmail also states that to fully pass DMARC you must either:
- Pass SPF Authentication and SPF Alignment, or
- Pass DKIM Authentication and DKIM Alignment.
Below is a table that summarizes the differences between the authentication and alignment requirements for SPF and DKIM:
Measure | What it checks | What it checks against | Pass result | Fail result |
|---|---|---|---|---|
SPF authentication | The [Return-Path] domain + the IP address that the message is from | The SPF record stored on the [Return-Path] domain | The SPF record authorizes the IP address that the email originated from | There is no SPF record containing the IP address that the email originated from |
SPF alignment | The [Return-Path] domain | That the domain matches the domain in your “From:” address on the email | The domains match | The domains do not match |
DKIM authentication | The [d=] domain inside the DKIM signature which is added by Marketo on send | The DKIM key stored on the domain that matches the domain set in the [d=] of the key in the email | They are a matching pair | They are not a matching pair |
DKIM alignment | The [d=] domain in the DKIM signature | That the domain matches the domain in your “From:” address on the email | The domains match | The domains do not match |
Measure | SPF authentication |
|---|---|
What it checks | The [Return-Path] domain + the IP address that the message is from |
What it checks against | The SPF record stored on the [Return-Path] domain |
Pass result | The SPF record authorizes the IP address that the email originated from |
Fail result | There is no SPF record containing the IP address that the email originated from |
Measure | SPF alignment |
|---|---|
What it checks | The [Return-Path] domain |
What it checks against | That the domain matches the domain in your “From:” address on the email |
Pass result | The domains match |
Fail result | The domains do not match |
Measure | DKIM authentication |
|---|---|
What it checks | The [d=] domain inside the DKIM signature which is added by Marketo on send |
What it checks against | The DKIM key stored on the domain that matches the domain set in the [d=] of the key in the email |
Pass result | They are a matching pair |
Fail result | They are not a matching pair |
Measure | DKIM alignment |
|---|---|
What it checks | The [d=] domain in the DKIM signature |
What it checks against | That the domain matches the domain in your “From:” address on the email |
Pass result | The domains match |
Fail result | The domains do not match |
Gmail also shared some helpful explanations of alignment with examples.
The simplest way to be compliant
If you use a standard Return Path at Marketo, the simplest way to meet the bulk sender requirements if you haven’t already, is to simply ensure you set up a custom DKIM Signature for the web domain that you use in your ‘From:’ address.
Since Marketo implements SPF for mktomail.com, you will pass SPF authentication. And even though you don’t have SPF alignment, you will have both DKIM authentication with DKIM alignment, thus meeting all the requirements.
If you use a custom Return Path, then you will also achieve SPF alignment as long as you use the Return-Path domain as your ‘From:’ address domain.
And while having both is not yet a requirement, it’s worth noting that Google states, “it’s likely that DMARC alignment with both SPF and DKIM will eventually be a sender requirement.”
It’s a great idea to start thinking about this now, as it could take some time to set up a Branded Return Path if you don’t have one already.
One-click unsubscribe requirement
| For all senders | For bulk senders |
|---|---|---|
Gmail’s requirement | ||
Yahoo’s requirement | Implement a List-Unsubscribe header, RFC8058 highly recommended |
| Gmail’s requirement |
|---|---|
For all senders | |
For bulk senders |
| Yahoo’s requirement |
|---|---|
For all senders | |
For bulk senders | Implement a List-Unsubscribe header, RFC8058 highly recommended |
Confusingly, this is not the unsubscribe link in the visible message, and it’s not about tokens or any other unsubscribe mechanism that you add to the normal visibly ‘body’ of your emails (though there are recommendations about those aspects — be sure to review both both the Gmail and Yahoo guidelines for these).
This requirement specifically refers to a hidden mechanism that is embedded in the Message Header. Email clients like Gmail or Yahoo can seek out this mechanism and turn it into Unsubscribe links that appear in the interface, like this one at the top of the message in Gmail:

Complying with particular requirements is definitely Marketo’s responsibility, and they currently add a type of these headers to all commercial messages on send (they won’t show up on transactional emails like receipts, and may not display on tests or samples).
However while Marketo’s current implementation means they are compliant with Yahoo’s requirement for bulk senders, they are not quite compliant with Gmail’s bulk sender requirements… yet.
Gmail’s bulk sender requirement is to conform to the standard known as RFC 8058. As per RFC 8058, a true ‘One-click unsubscribe’ setup looks like this, with an HTTPS address as the unsubscribe mechanism:
List-Unsubscribe: https://example.com/unsubscribe/functionality
List-Unsubscribe-Post: List-Unsubscribe=One-Click
Marketo currently embed a simpler one-line ‘List-Unsubscribe’ using a mailto address as the mechanism, looking a little like this:
List-Unsubscribe: mailto:abc123@unsub-abmktomail.com
As per Marketo’s official guidance here, they are still in the process of meeting this requirement.
“For Marketo Engage, Adobe … does not currently support the “http/URL” option. Further updates on that to come.”
We contacted Marketo about this, and they recommended bookmarking the post and checking back regularly for updates.
Gmail’s FAQs on the topic actually says that, “senders that already include an unsubscribe link in their messages have until June 1st 2024 to implement one-click unsubscribe in all commercial messages.” It’s unclear whether they are referring here to a visible link in the body of the email, or a simpler List-Unsubscribe header, but either way it sounds like Marketo likely have until June 1st to comply with this one.
Processing time for unsubscribes
Yahoo requires that bulk senders honor unsubscribes within 2 days, while Gmail places an emphasis on one-click unsubscribe for bulk senders, which should be immediate.
Marketo states that even with their current method, they already process unsubscribes instantly, so they are compliant with this requirement.
Custom unsubscribe configurations
If you have any custom unsubscribe flows that aren’t using the standard Marketo implementation then be sure to refer to the official guidance from both Gmail and Yahoo and make sure they are all compliant with the new rules.
| Gmail’s requirement |
|---|---|
For all senders | Ensure that sending domains or IPs have valid forward and reverse DNS records |
For bulk senders | Ensure that sending domains or IPs have valid forward and reverse DNS records |
| Yahoo’s requirement |
|---|---|
For all senders | Have a valid forward and reverse DNS record for your sending IPs |
For bulk senders | Have a valid forward and reverse DNS record for your sending IPs |
PTR Records, aka Reverse DNS Records
We contacted Marketo regarding PTR records and they confirmed that they do publish PTR or Reverse DNS records for all the IP addresses that they manage.
Monitoring your IP Address/es
Gmail suggests that you use their tools to monitor reputation on shared IPs. And while it’s not a technical requirement, both Gmail and Yahoo suggest that you segregate email types by IP address or DKIM domain.
The responsibility for all these requirements can depend on whether you use a shared or dedicated IP. If you remain on a shared IP then this remains Marketo’s responsibility, if you are on a dedicated IP then some of these requirements will fall on your organization’s shoulders.
Use a TLS connection for transmitting email
Gmail’s requirement is that TLS be used for all senders. According to Marketo’s Security Overview whitepaper, they are compliant with this requirement from Gmail. The white paper states:
“Marketo Engage uses HTTPS TLS v1.2 to protect data in transit.”
Refer to page 6 of the Adobe® Marketo Engage Security Overview for more information.
Wrapping up
We hope this guide has helped to clarify some of the key technical requirements for bulk senders that Gmail and Yahoo are introducing in 2024, as well as what they mean for you and your team as Marketo users.
As always, things can change fast, so be sure to bookmark Marketo’s official guidance and check back regularly for any changes from them. Likewise, we have already seen quite a few updates to the official guidance from both Gmail and Yahoo so be sure to keep a keen eye on those too.
Frequently Asked Questions
Starting February 2024, Gmail requires bulk senders to implement both SPF and DKIM authentication, publish a DMARC policy (even with no enforcement), and enable one-click unsubscribe functionality. These measures aim to verify sender identity and reduce spam.
Yes, both Gmail and Yahoo now require bulk senders to publish a valid DMARC policy. While enforcement isn’t mandatory, having the policy in place is essential to comply with their updated sender requirements.
SPF verifies that the sending IP is authorized by the domain, DKIM ensures email integrity via cryptographic signatures, and DMARC enforces sender policies while aligning “From” addresses with SPF or DKIM. Together, they prevent spoofing and improve inbox placement.
Gmail defines a bulk sender as any domain sending over 5,000 messages per day to Gmail or Googlemail addresses. Once this threshold is crossed, stricter authentication and compliance requirements apply.
In Gmail, open the message, click the three-dot menu, and select “Show original.” You’ll see authentication results for SPF, DKIM, and DMARC at the top of the message header. Look for lines like spf=pass, dkim=pass, and dmarc=pass.